Author: Mike Manzotti – Principal Consultant at Dionach
Changes in the threat landscape combined with the needs of the modern enterprise often come with the requirement for IT staff to be able to respond to cyber security incidents 24/7. These changes have forced many organisations to outsource the detection and response to these incidents to third-party Security Operation Centre (SOC) providers, which offer round-the-clock services to multiple organisations.
However, how can you evaluate a SOC? How can you be confident that that an external SOC or your internal Blue Team is detecting well-known cyber-attacks, let alone sophisticated campaigns directly targeting your company and its employees? Many SOCs provide a trial period whereby you can try their services but how do you know if your investment is worth the money?
Purple Team assessments are arguably the best method of evaluating SOCs or Blue Teams. Below, we’ll take a look at what a Purple Team assessment is, the process for how they are carried out, and how they compare to other assessment frameworks.
What is a Purple Team Assessment?
A Purple Team assessment will measure your detection and response capabilities by executing pre-defined attacks that are designed to mimic real cyber threats. These attacks, agreed prior the engagement, allow the organisation to have an assessment completely tailored to their environment, goals, and playbooks, as well as allowing a comparison against desired outcomes and stated aims.
Since several attacks scenarios can be played out as part of the exercise, it can often be more efficient to exclude those are not relevant to the organisation, and only to include popular and common attacks that match with the risk profile of the organisation. The pre-defined attacks are a simulation of adversary Tactics, Techniques and Procedures (TTPs) used by Advanced Persistent Threats (APTs). TTPs are mapped by an internationally recognised framework, known as MITRE ATT&CK.
The Process
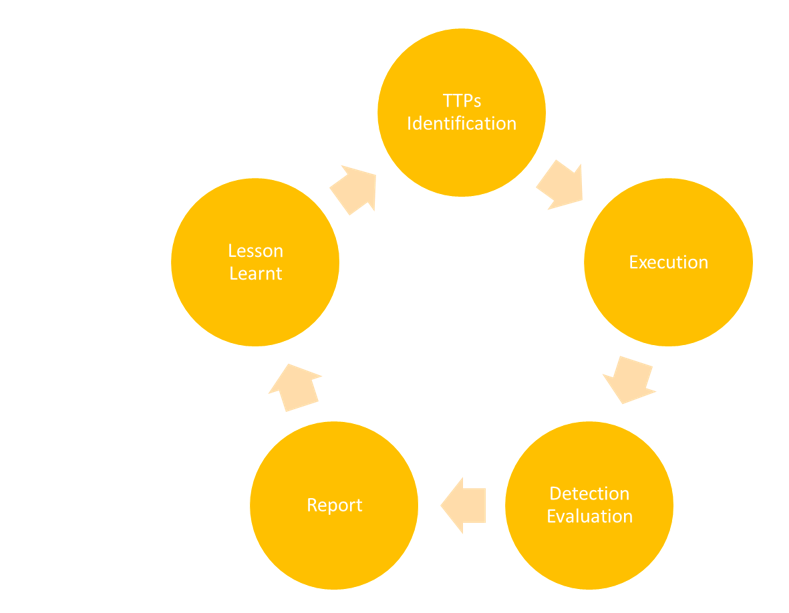
The number and category of TTPs will vary depending upon the agreed scope; however, Purple Team Assessments will typically include the following steps:
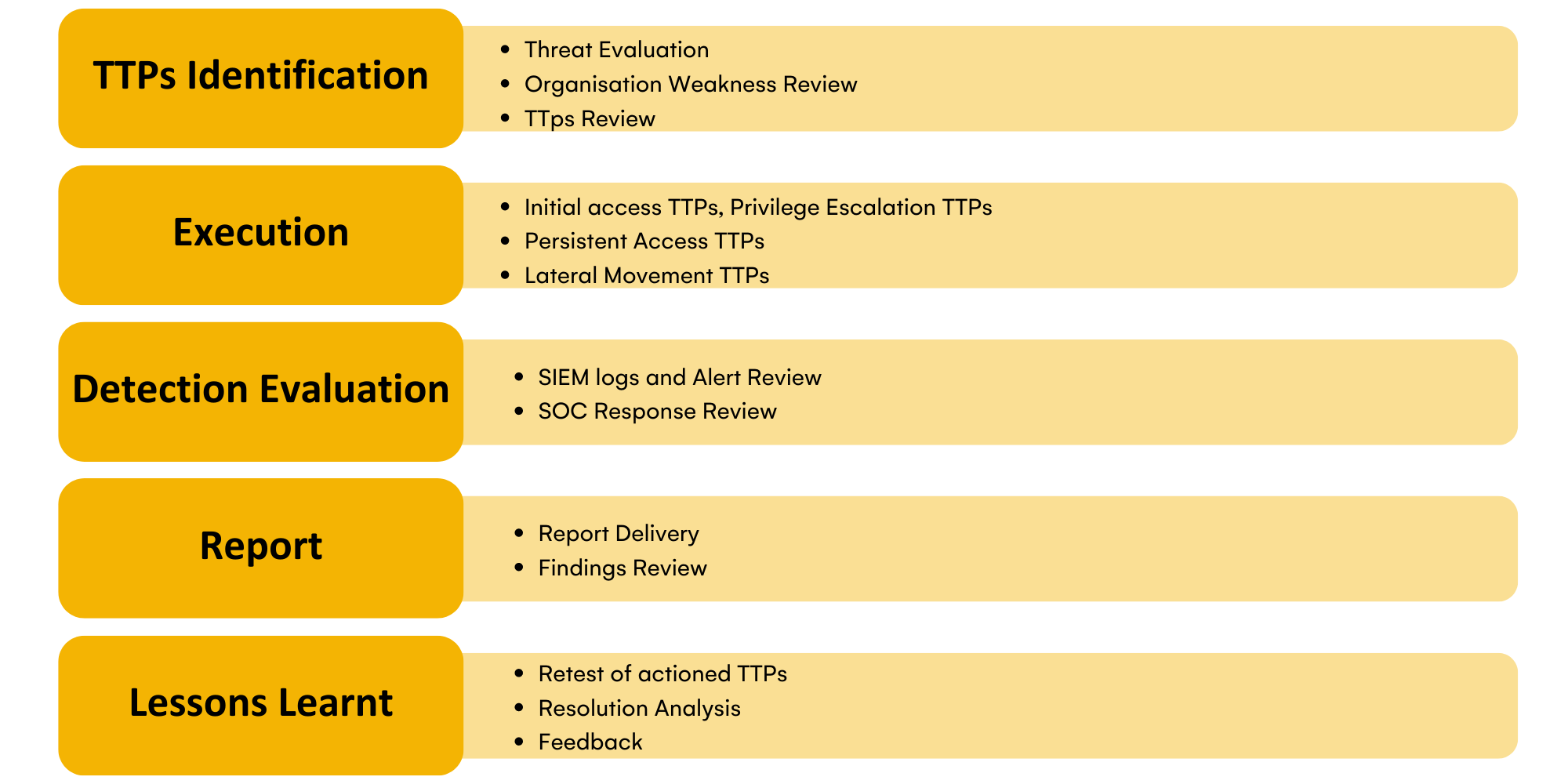

One big advantage of performing a Purple Team assessment is that they can easily be repeated over a short period of time by executing the same TTPs. The results will provide a clear indication of any improvements in detection and response capabilities over a period of time.
Additionally, multiple, consistent Purple Team assessments performed over a period of time will ensure that actioned TTPs are correctly detected and responded to accordingly and in-line with the organisation’s policies and procedures.

Red Team Assessments Vs Purple Team Assessments
At first glance, Red Team and Purple Team assessments might look very similar but there are significant differences between the two services. The following table highlights the main ones:
| Red Team Assessment | Purple Team Assessment | |
| Approach | Opportunistic approach.Red Team will take advantage of vulnerabilities that would allow an adversary to compromise systems and resources. | Collaborative approach.TTPs are pre-defined by the Purple Team and Blue Team. |
| Visibility | Only a small number of individuals are aware of the Red Team, or sometimes just the CTO. Blue Team or SOC are not aware of the assessment.Results are shared across Blue Team and Red Team only when the assessment is complete. | Blue Team or SOC are aware of the assessment.Results are shared across Blue Team and Red Team during and when the assessment is complete. |
| Goal | Prove that sensitive data and systems can be compromised, and test detection and response capabilities. | Test detection and response capabilities measured in a controlled manner, allowing improvements to be measured over a given time period. |
| Scope | Entire organisation. All possible attack vectors are permitted. | Pre-defined TTPs. Usually these are tailored to the business model of the organisation. |
| Duration | Usually spanned over a period of 3 months, subject to agreed objectives. | Dependent on the number of TTPs selected and any custom objectives. |
| Output | Detailed report on how the organisation has been compromised. Feedback on detection and response capabilities based solely on the discovered vulnerabilities exploited during the exercise. | Detailed report on all pre-defined TTPs indicating whether they have been detected, blocked, or investigated.The repeatable model of Purple Team exercises also allows an organisation to see measured improvement over time. |
| Main Benefits | Mimic a realistic cyber security attack. Best tool to evaluate current overall cyber security posture. | Provide an accurate metric to measure improvements on detection and response capabilities. Best tool to evaluate SOC and Blue teams. |
Traditional Penetration Tests Vs Purple Team Assessments
It is also worth comparing traditional penetration testing with purple team assessments.
| Penetration Test | Purple Team | |
| Approach | White or black box approach. When a white boxpen test is performed, all information is shared with the tester. Conversely, when a black box test is carried out, only details of the target scope are provided. | Collaborative approach. TTPs are pre-defined by the Purple Team and Blue Team. |
| Visibility | IT Team and developers are aware of the test. Results are shared with the IT team and developers when the test is complete. | Blue Team or SOC are aware of the assessment. Results are shared across Blue Team and Red Team during and when the assessment is complete. |
| Goal | Identify as many vulnerabilities as possible within a given scope, and within an agreed time frame. | Test detection and response capabilities measured in a controlled manner, allowing improvements to be measured over a given time period. |
| Scope | The scope is defined by the organization requesting the penetration test and can be as small as a single external IP address. | Pre-defined TTPs. Usually these are tailored to the business model of the organisation. |
| Duration | Depending on the size of the scope. | Dependent on the number of TTPs selected and any custom objectives. |
| Output | Detailed report on the vulnerabilities identified within the given scope. There is no testing of detection and response capabilities. | Detailed report on all pre-defined TTPs indicating whether they have been detected, blocked, or investigated. The repeatable model of Purple Team exercises also allows an organisation to see measured improvement over time. |
| Main Benefits | Good tool for evaluating the security of a single application or network. | Provide an accurate metric to measure improvements on detection and response capabilities. Best tool to evaluate SOC and Blue teams. |
A summary of Purple Teams Assessments
In Summary, a Purple Team Assessment does the following:
- Identifies gaps in existing detection and response capabilities;
- Emulates real word attacks through TTPs;
- Evaluates the performance of SOCs and Blue Teams;
- Provides an accurate way to measure improvements in response and detection capabilities using industry standard frameworks.
How do I Book a Purple Team Assessment?
If you would like to discuss Purple Team assessments in more detail, or if you would be interested in a quote, please contact us here.



